Petya Ransomware- A Malicious Virus to Harm Your System & Its Data
Horror! Now, there is an another threat for the organizations after WannaCry- Petya Ransomware. This destructive software has already struck systems in more than 60 countries. Yes, there are many companies in US and Europe, which are crippled by this deadly malicious code. It is the second key global cyber attack in the past 2 months. Lets us discuss the details of this destructive code and the know how to escape from its attack.
What Petya is?
It is dissimilar as compared to the other ransomware spreading these days. It does not encrypt the file one by one but denies access to the entire machine by targeting low-level structures on disk. The creators of this destructive virus have brought forth their boot loader with a small kernel that is 32 sectors elongated.
First Place of Identification
Ukraine is the first place, where approximately 12,500 systems encountered this malicious program, declared by Microsoft. After this, it is observed in other 64 countries. These countries include Brazil, Germany, Belgium, Russia, and the United States.
According to the Microsoft, this infection is initially traced to tax accounting software from a Ukrainian’s company.
This malicious software is still affecting the airports & ATMs of Ukrainian. It is also hampering the international business from a shipping giant to a drug company.
Why is this Ransomware called Petya?
The malware seems to share a major quantity of code with the older piece of malignant code, which was called Petya. However, after some hour of its outbreak researchers noticed that the resemblance is skin deep only. The security researchers at Russia re-dubbed it as NotPetya & increasingly tongue-in-cheek alternate of that name: Pneytna, Petna, and etc. began to spread.
How Does Petya Cyber Attack Spreads and Works??
Petya ransomware spread via large firms, which includes the food company Mondelez, advertiser WPP, legal firm DLA Piper, & Danish shipping and transport firm Maersk. It results in the encrypted PCs and data. Later, to decrypt the data a certain amount of ransom is required.
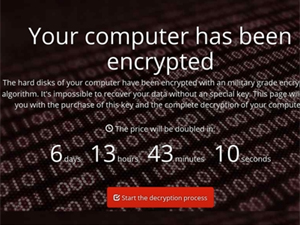
This malware takes the control over machines and then demands $300, paid in Bitcoin to recover the encrypted hard drives and files. It is extending quickly across a company after a system gets infected with the help of EternalBlue vulnerability in MS Windows. Moreover, it can also spread via two MS Windows administrative tools. It attempts the first option and in the case of failure move towards the next. In addition, the system may get shut down at the time of these cyber attacks. Apart from the file encryption, it also overwrites and encrypts MBR (Master boot record).
File Encryption
Petya performs the encryption in two modes:
- User Mode: Once this malicious code, Petya, spread to multiple computers, user-mode encryption happens where only the specific extension files are encrypted on the disk.
- Full Disk: The MBR is changed for adding a custom loader that is helpful in loading CHKDSK. This stimulator helps in hiding the fact that the disk encryption is happening. It occurs once the user mode encryption is done.
Stages of Data Encryption
- Stage 0 “MBR Overwrite”– Overwrite hard drive’s Master Boot Record & inserting custom boot-loader.
- Stage 1 “MFT Encryption”– Usage of custom boot-loader, which is introduced in stage 0 for the encryption of all Master-File-Table. This renders the file of the system entirely unreadable.
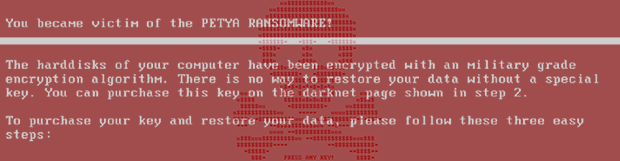
- Stage 2 “Ransom Demand”– Shows the logo of Petya and a ransom note displaying what must the user do for the decryption of the hard-drive.
Petya Ransomware Attack: How to Escape from this Virus
These are some actions, which may help in the prevention of Petya Cyber Attack as mentioned below:
- Block Source E-mail Address
wowsmith123456@posteo.net - Block the Following Domains
- http://mischapuk6hyrn72.onion/
- http://petya3sen7dyko2n.onion/
- http://petya3sen7dyko2n.onion/MZ2MMJ
- http://petya3jxfp2f7g3i.onion/
- http://french-cooking.com/
- http://mischa5xyix2mrhd.onion/MZ2MMJ
- http://petya3jxfp2f7g3i.onion/MZ2MMJ
- http://benkow.cc/71b6a493388e7d0b40c83ce903bc6b04.bin COFFEINOFFICE.XYZ
- http://mischapuk6hyrn72.onion/MZ2MMJ
- 95.141.115.108
- 84.200.16.242
- 111.90.139.247
- a809a63bc5e31670ff117d838522dec433f74bee
- 1b83c00143a1bb2bf16b46c01f36d53fb66f82b5
- 078de2dc59ce59f503c63bd61f1ef8353dc7cf5f
- 0ff07caedad54c9b65e5873ac2d81b3126754aac
- d5bf3f100e7dbcc434d7c58ebf64052329a60fc2
- 7ca37b86f4acc702f108449c391dd2485b5ca18c
- 2bc182f04b935c7e358ed9c9e6df09ae6af47168
- aba7aa41057c8a6b184ba5776c20f7e8fc97c657
- 82920a2ad0138a2a8efc744ae5849c6dde6b435d
- bec678164cedea578a7aff4589018fa41551c27f
- 51eafbb626103765d3aedfd098b94d0e77de1196
Final Words to Conclude
As the usage of the internet or digital things is becoming more intense, several ransomware attacks are also increasing. The creators of malicious software are getting more innovative to encrypt the system files and the crucial data of a user. One such new harmful application is Petya ransomware, as discussed above. Just like the other malware, this harmful virus locks the computer and its files too. However, this malignant software comes up with a better mechanism to spread itself than WannaCry. So it’s better to encrypt your computer systems and files, to stay away from these kinds of harmful cyber attacks.